In this article
To add user-assigned managed identity
You can use Azure Key Vault to securely store and control access to tokens, passwords, certificates, and API keys. For more information see Microsoft's About Azure Key Vault.
To add passwords to Key Vault
- Create a Key Vault on the Azure portal.
- Store the password in the Key Vault's Secrets.
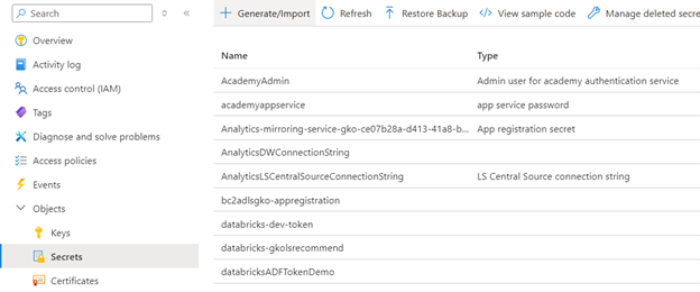
- Grant Azure Data Factory (ADF) permissions to list and get secrets (use the system-assigned managed identity).
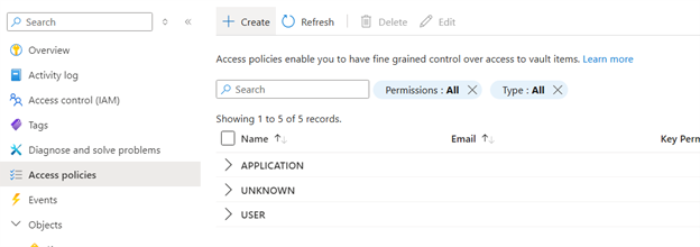
- In the Azure Data Factory (ADF) create a Linked service:
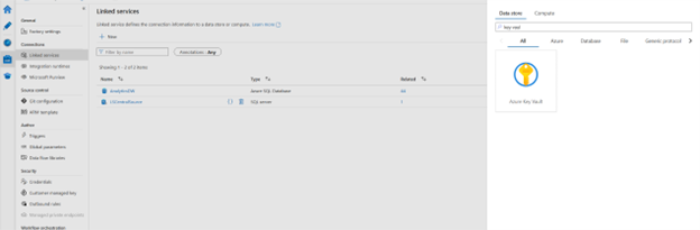
- Change the password field in the AnalyticsDW and LSCentralSource to Azure Key Vault.
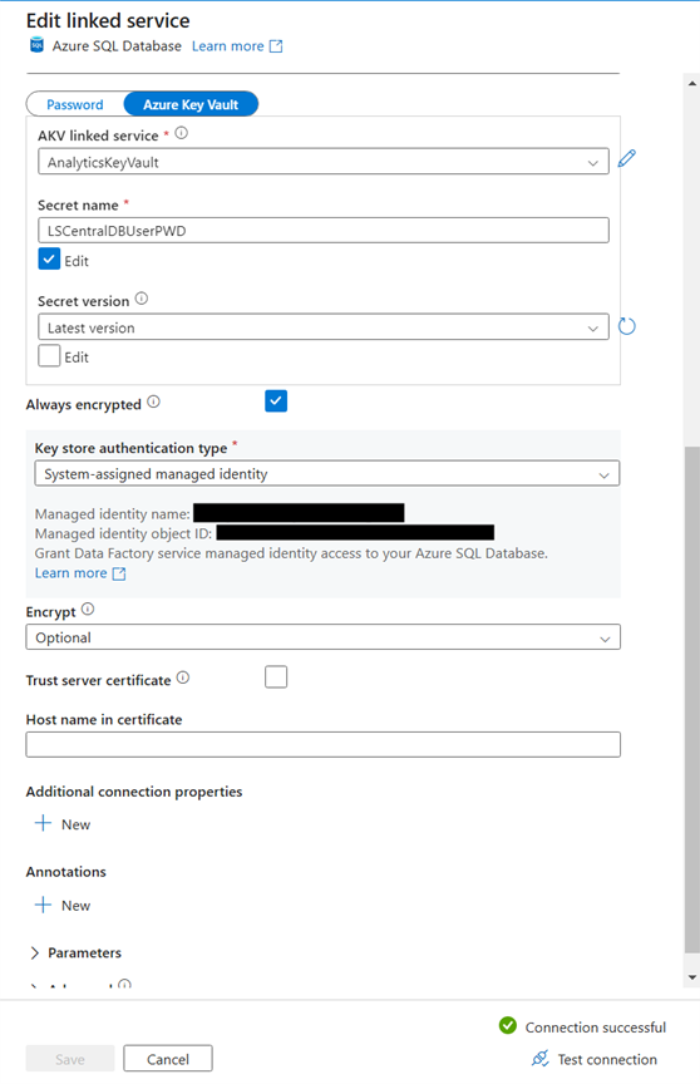
- Fill in the AKV linked service field and Secret name that you set up earlier when you stored the password in the key vault
- Select a Key store authentication type. For more information see Manage user-assigned managed identities.
- Test the connection.
See also Microsoft's Store credentials in Azure Key Vault.
To add user-assigned managed identity
The Azure preferred method for Key Store authentication type is Managed identity authentication. This is also the method LS Retail recommends for Analytics Data Warehouse.
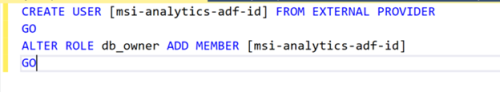
- Create Credentials in the Azure Data Factory that references the user-assigned managed identity, and publish.
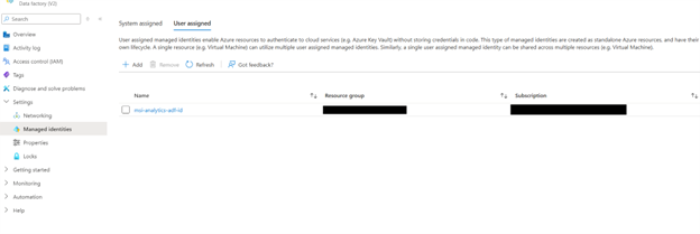
- In the Analytics Data warehouse, login with your Entra ID admin user, and create a new user for the Managed identity.
Note: The username and managed identity name must match.
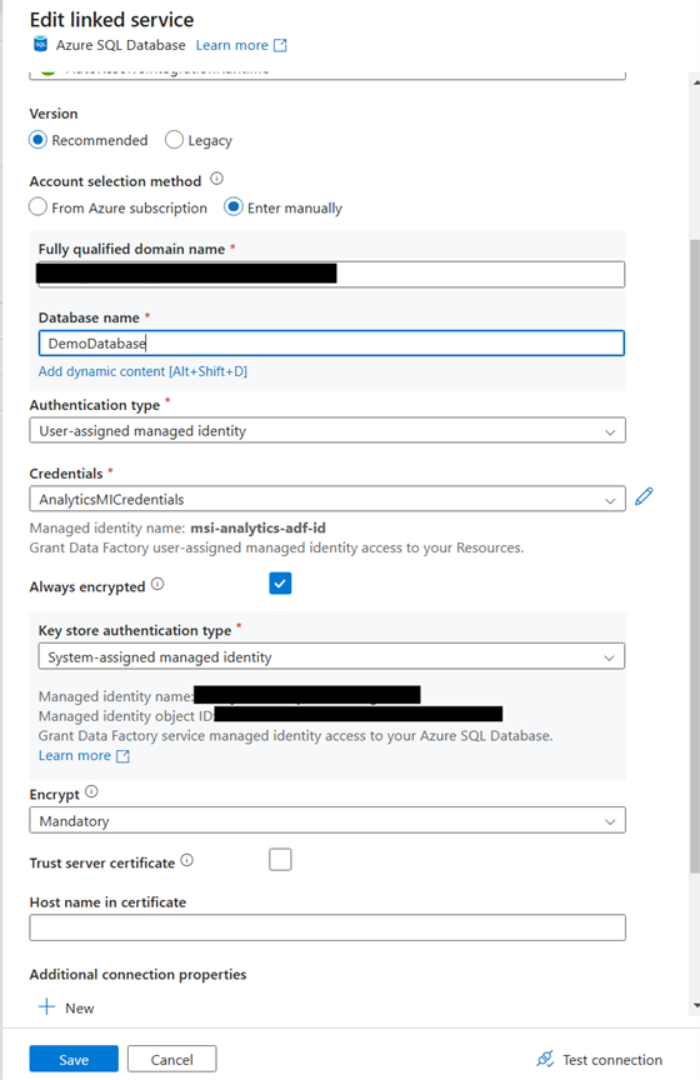
Change the AnalyticsDW linked service to Authentication type “User-assigned managed identity”, and select the credentials you created earlier.
Note: You can delete the username and password parameters from the linked service definition.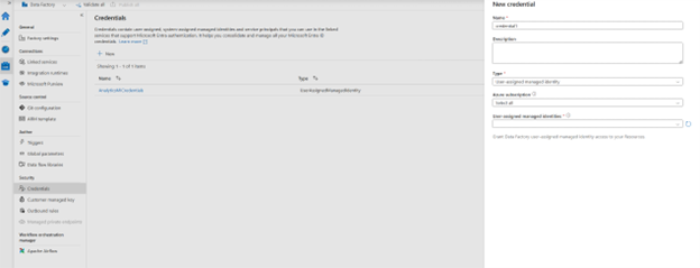
- Publish the changes, and then test the connection.
For more details see Microsoft's Manage user-assigned managed identities.